Phishing vs. Spear Phishing Attacks
Most companies know to look out for phishing attacks. However, spear phishing attacks are a more targeted approach to stealing information from staff at a specific business. However, that doesn’t make regular phishing any less of a threat. These types of scams have been slipping into inboxes for years and have claimed tons of victims as it is the most popular form of attack from hackers.
Spear phishing attacks are a targeted approach to stealing information from staff at a specific business and WTS can help.

These attacks have a lot in common but they are distinctly different in their approach and goals. The biggest difference between the attacks is who they target and how they are strategized. General phishers use urgency to manipulate receivers, but spear phishers design their scam to gain the trust of the recipient. Our cybersecurity services can help prevent both.
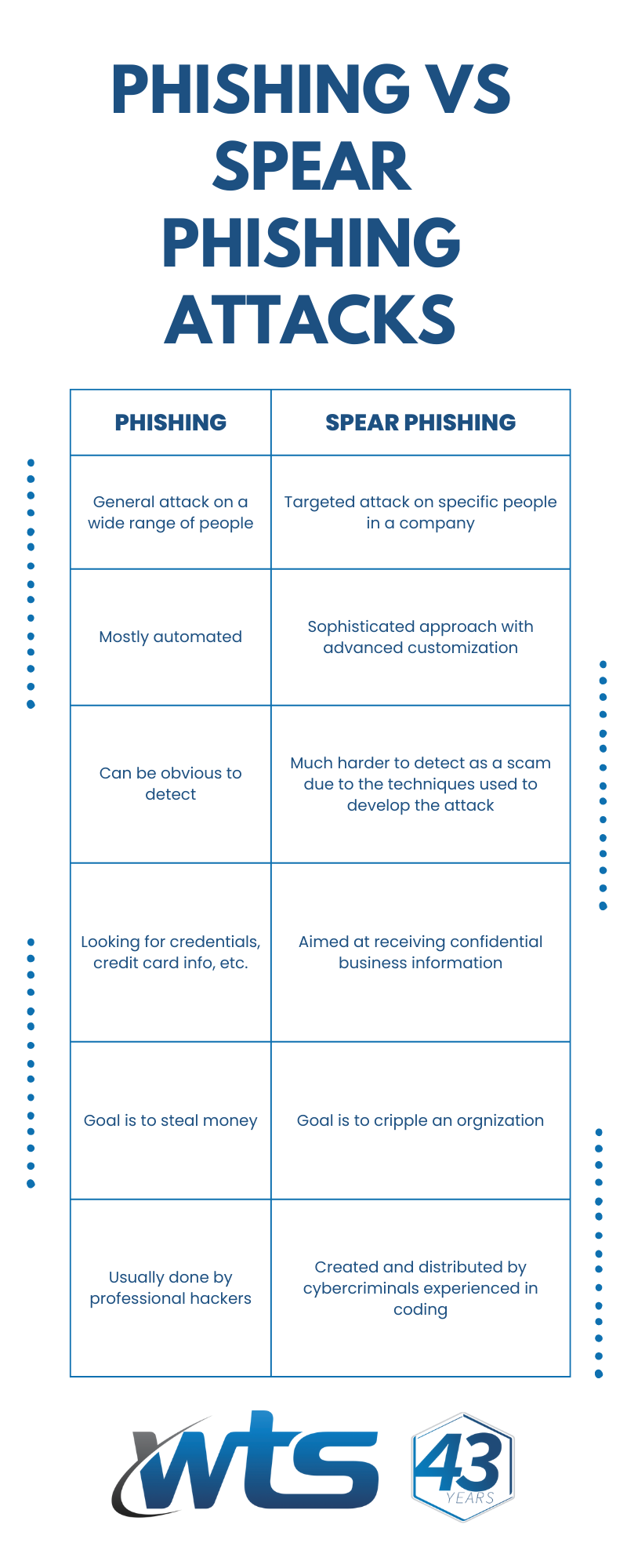
Phishing Attacks involve emails with malicious attachments or links designed to steal personal or business information. Phishing is one of the most common forms of cyber threats as they are used to scam masses of people at one time. Out of thousands of emails sent out, they expect only a small portion to take the bait. Spear phishing is a specific and more targeted attack on select victims, but both are used to spread malware and gain valuable business information.
Spear Phishing Attacks follow the same pattern as normal phishing attacks but cybercriminals choose their targets more specifically when it comes to spear phishing. The attackers research their target to make their attempt more personalized and take on the disguise of trusted sources that people are less likely to question. An email may seem to come from business partners or colleagues that need your help.
How to Detect and Prevent Spear Phishing Attacks
1. Be Suspicious
Reading these details, it may seem easy to detect a phishing and spear phishing email now, but the actual attacks can be difficult to identify on a busy workday. The best way to avoid being a victim of these cybercrimes is to be suspicious of every email.
2. Verify the Sender
Before responding to any email, check the email address to make sure you’re communicating with who you are intending to. To review the email address, click on the name of the sender and make sure the full email address that sent the email and the one that will receive the reply are spelled correctly. If they are not the usual point of contact, there is reason to be suspicious. In which case, confirm the identity of the sender by contacting them in a different manner (like a phone call).
3. Verify Links
Email addresses can be spoofed and hacked, so even if the sender looks legit make sure to review any links in the email before clicking on them. Hover your mouse over the link and your computer will show you where that link will take you in the bottom left corner of the browser screen. If the URL is different from the text in the embedded link or the expected website, don’t click on it.
4. Use Anti-Virus Software
Having anti-virus software downloaded on your computer is essential to avoid downloading malware. This kind of protection software will scan the attachment before it’s downloaded to your computer to make sure it’s safe. It’s also best not to open attachments unless you know what it is, who it’s from, and you’re expecting to receive them.
Let’s talk. Contact our team at 843-236-6436.
Ready for IT that WORKS for your business?

- Managed IT Services
- Business Phone Systems
- Managed Print
- Cybersecurity
- Cloud Services
- Data Cabling
Schedule a 15-minute meeting with our team.
